Disclaimer: This is not a full, well-written write-up.
Just some notes about how I solved the challenge.
TL;DR: https://gist.github.com/dustty0/f8c501d805441f399aec3c08ebe7c787
Stage 0. E-mail & attached .html file
The provided .eml file contains a html file.
It contains obfuscated Javascript payload, and drops a zip file containing a single js file.


Stage 1. Javascript (1)
[TOP SECRET] Arodorian Hypercraft.pdf.js
It’s just obfuscated Javascript file.
Slightly modifying and running the script will drop the second stage.
stage1.js
Stage 2. Javascript (2)
stage2.js
Similar to the stage 1, stage 2 is an obfuscated Javascript file.
By running the script line by line, we can get the next stage’s payload.
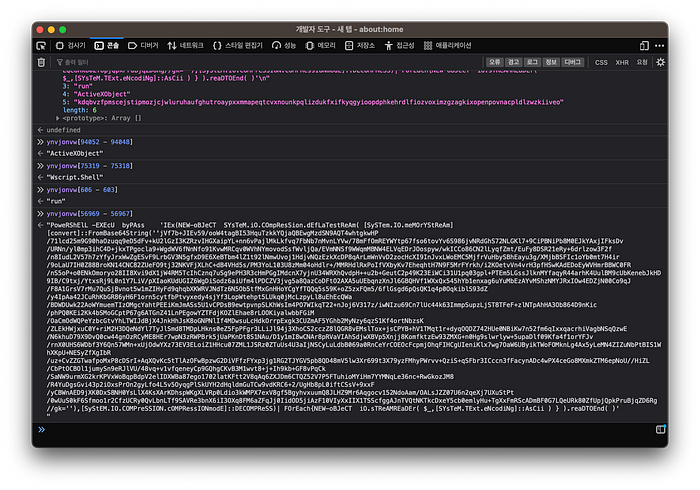
Stage 3. Powershell (1)
Stage 2 will try to run an obfuscated Powershell script.
stage3.ps1
Simply removing the -execu bypass flag and running the script will drop the next payload in plaintext, without invoking it.
Stage 4. Powershell (2)
stage4.ps1
Stage 4 is also an obfuscated Powershell script.
After removing unnecessary codes, we get the script below which prints the flag:
SET-ItEM ("VAr"+"Ia"+"B"+"le:4z0") ([TypE]("{2}{3}{1}{0}" -f'odinG','.enC','sYSTEm.T','ext') ) ;
function UYc`xq (${TN`me},${Chk`go`Iul}) {
for (${eum`lMx`NyUg} = 0; ${eu`mL`MxNYug} -lt ${T`NME}."c`OUnt"; ${Eu`MLMx`NyUG}++) {
${T`NME}[${eUM`lM`XnyuG}] = (${t`NmE}[${eUm`Lmx`N`yuG}] -bxor ${c`HKGo`iUl})
}
return ( gEt-vaRIAble ("4"+"Z0") -VaL)::"As`Cii"."gETs`T`RIng"(${tN`Me})
}
(&("{2}{1}{0}" -f 'q', 'cx', 'UY') ([System.Byte[]] @(0x97,0x8b,0x9d,0xa4,0xb3,0xef,0xab,0xac,0x80,0xb0,0xb9,0x80,0xb3,0xeb,0x86,0xec,0xad,0xac,0x80,0xb6,0x91,0x80,0xab,0xb7,0xeb,0xab,0x80,0xee,0xa2)) 223)HTB{l0ts_of_l4Y3rs_iN_th4t_1}
